- WhatsApp has introduced a new security layer for users using Rust to enhance protection against malware threats.
- WhatsApp’s deployment of the media consistency library in Rust to billions of devices globally demonstrates Rust’s readiness for large-scale production.
Our Media Handling Strategy
WhatsApp offers default end-to-end encryption to secure messages for over 3 billion users daily. The online security landscape is adversarial, and we continuously adapt our strategy against cybersecurity threats while supporting the WhatsApp infrastructure to facilitate connections.
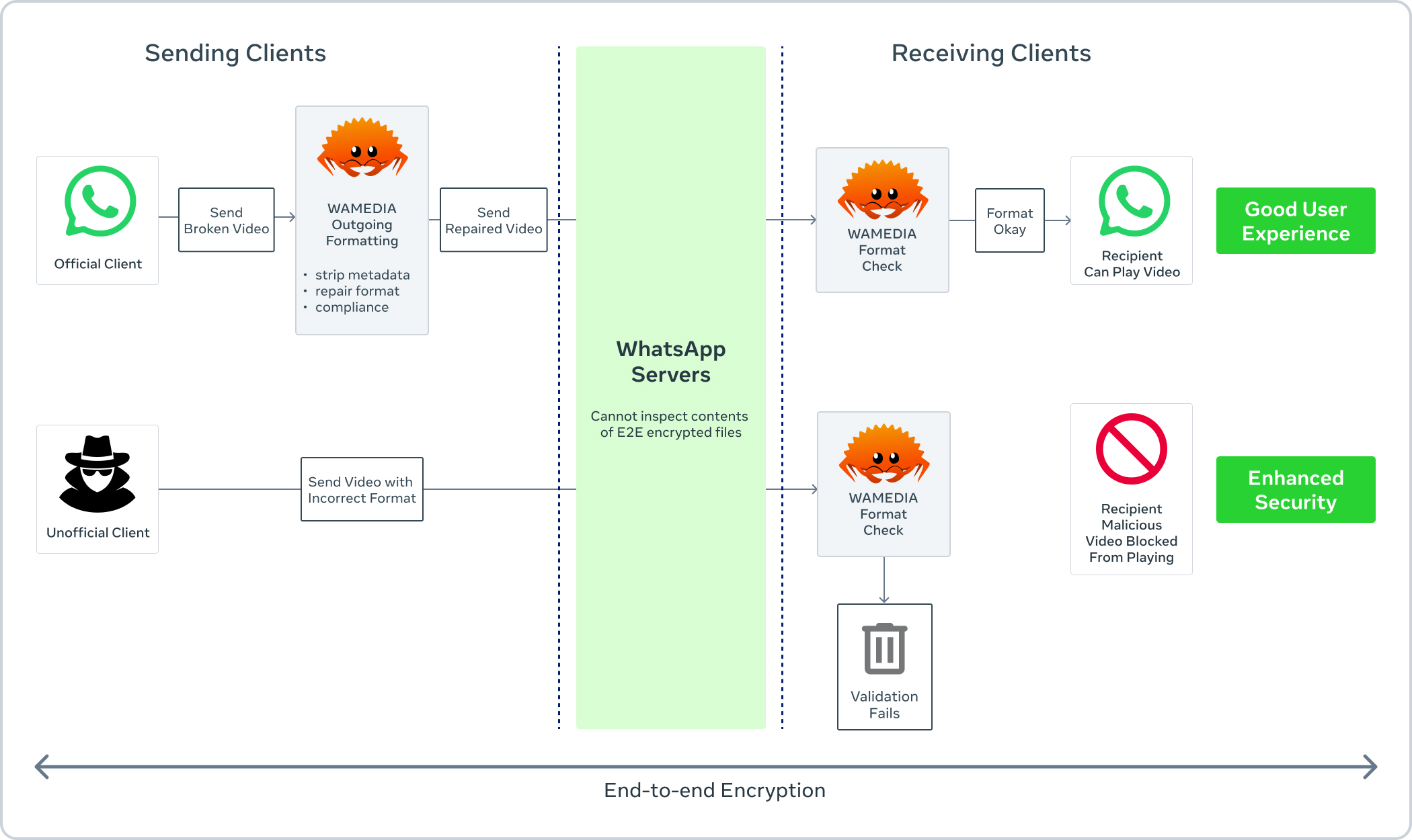
WhatsApp allows users to share media and documents, with warnings for dangerous attachments like APKs. Rare malware may hide in benign files like images or videos, targeting vulnerabilities in operating systems, libraries, or apps.
To counter such threats, WhatsApp increasingly uses Rust in media sharing features. Rust’s memory safety provides numerous security benefits. We believe this is the largest global rollout of a Rust-written library.
To explain this rollout, we revisit a critical OS-level vulnerability that prompted WhatsApp to strengthen media-sharing defenses.
2015 Android Vulnerability: A Wake-up Call for Media File Protections
In 2015, Android devices and their apps were vulnerable to “Stagefright”. This bug in the media file processing by OS libraries could not be patched by apps. Due to delayed software updates, we sought solutions to keep users safe despite OS vulnerabilities.
A cross-platform C++ library developed by WhatsApp to format MP4 files, “wamedia”, was modified to detect non-standard files that might exploit OS library bugs, protecting users from Stagefright vulnerability faster than OS updates.
Realizing that media checks process untrusted inputs automatically, we identified wamedia as an ideal candidate for a memory-safe language.
Our Solution: Rust at Scale
Instead of rewriting, we developed the Rust version of wamedia alongside the original C++ version, using differential fuzzing and tests for compatibility.
Challenges included binary size increase due to the Rust standard library and build system support for WhatsApp’s diverse platforms. We built this support and replaced 160,000 lines of C++ with 90,000 lines of Rust. The Rust version had performance and memory usage advantages over C++. Rust was rolled out to all WhatsApp users on multiple platforms, proving its role in app and user security.
We added more checks for non-conformant file structures to protect libraries from parser exploit attempts and flagged high-risk file types for warning. Known dangerous file types are flagged for special handling. This “Kaleidoscope” system protects WhatsApp users from malicious clients and attachments. While not a complete solution, it mitigates many attacks.
Each month, these libraries are distributed to billions of devices on WhatsApp, Messenger, and Instagram, marking the largest deployment of Rust code globally. This underscores Rust’s production-readiness and value on the client-side.
How Rust Fits In To WhatsApp’s Approach to App Security
This reflects WhatsApp’s investment in security, including end-to-end encryption for messages and calls, encrypted backups, key transparency technologies, and more.
WhatsApp reports CVEs for significant issues found, enabling users to protect themselves through prompt advisories and updates.
Security is ensured by identifying and assessing risk sources through audits, fuzzing, static analysis, supply chain management, and automated attack surface analysis. We expanded our Bug Bounty program with a WhatsApp Research Proxy to facilitate network protocol research.
Risk reduction follows risk identification. Most high severity vulnerabilities arose from memory safety issues in C and C++ code. We employ three strategies:
- Design products to minimize unnecessary attack surfaces.
- Invest in security assurance for remaining C and C++ code.
- Default to memory-safe languages for new code, not C and C++.
WhatsApp added protections like CFI, hardened memory allocators, safer APIs, and more. C and C++ developers receive specialized training, development guidelines, and automated security analysis. There are strict SLAs for addressing identified issues.
Accelerating Rust Adoption to Enhance Security
Rust enabled WhatsApp’s security team to create a secure, high-performance, cross-platform library ensuring consistent and safe media sharing. This advances behind-the-scenes security and is part of our defense-in-depth strategy. WhatsApp and Meta security teams are promoting Rust adoption for impactful security enhancements, anticipating increased Rust use in the future.