When it comes to safeguarding your business against security threats, a singular solution won’t suffice; attackers are ever-evolving and innovating.
The threats today have increased in scale and sophistication, with attackers becoming more adept at accessing sensitive data.
As new security measures emerge, attackers devise new (or even old) strategies to counter these defenses. Thus, it’s vital to understand the current threat landscape and how attackers adjust their tactics.
This article explores the evolution of attacks in recent years and ways you can better protect your organization.
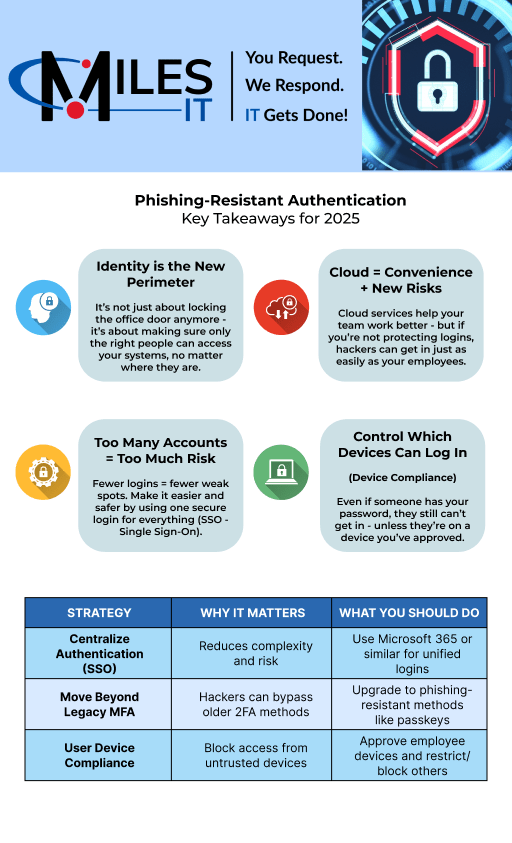
**“Identity is the New Perimeter”**
For years, securing an organization’s IT perimeter was deemed the optimal strategy for preventing unauthorized access to emails, business applications, and sensitive information.
There was a common belief that a strong firewall or similar device at the network’s edge would deter attackers.
While these devices are essential for basic security (like preventing outsiders from accessing internal applications), there is often overdependence on them.
Since COVID-19, there’s been a significant shift in business operations. Many employees now work remotely.
This shift is logical—employees desire to work from anywhere without hindrance, and business owners benefit by recruiting talent from any location.
Responding to this demand, cloud service adoption, like Microsoft Office 365, has surged over the past decade. Consequently, businesses increasingly rely less on internal network infrastructure.
Cloud hosting offers notable security advantages over local servers:
– Automatic patches
– High availability
– Rapid scalability
However, since cloud applications are accessible globally, attackers can attempt to authenticate if they steal an employee’s digital identity.
Previously, locally hosted infrastructure provided attackers numerous avenues for external access.
If an application isn’t regularly patched, known vulnerabilities can enable direct access to the main server. With this avenue closing for attackers, they now focus on phishing company users using various techniques, often successfully.
Once inside an account for a major cloud-hosted application, attackers can access emails and sensitive information.
What does this imply?
A significant shift towards protecting digital identities is essential to stay ahead of attackers.
**Centralize Authentication**
The more accounts you have, the greater the “attack surface” your organization presents.
“Attack surface” refers to how many assets your organization maintains, such as accounts, software, services, and staff. Each asset represents an entry point for attackers.
The more you protect, the more entry points a threat actor can exploit.
Several challenges arise in safeguarding these accounts:
– Password strength
– Enforcing multi-factor authentication
– Permissions and roles
– Account removal when staff leave
Given the volume of accounts needing management, security uniformity becomes a substantial challenge for mature organizations.
**The solution: centralize login options whenever possible.**
Single sign-on enables applications to leverage an external provider, like employee email accounts. Users log in to applications with a single account.
It often involves a single sign-on to platforms like Microsoft Office 365, enhancing security and convenience by reducing multiple logins daily.
**Multi-Factor Authentication Alone is No Longer Enough**
For years, security experts have advocated multi-factor authentication (MFA) on accounts to guard against phishing and account takeover.
MFA remains vital for protecting sensitive data and is often the initial recommendation for security improvement.
MFA serves as a backup form of authentication if a password is compromised, offering an extra layer of security.
However, the effectiveness of MFA against phishing has lessened.
Recently, attackers have devised methods to phish users with MFA via proxy connections to legitimate services. These attacks are “Adversary in the Middle” (AiTM) attacks.
AiTM phishing attacks have risen, yielding significant success for threat actors.
In an AiTM attack, even if using a rolling code or text message for two-factor authentication, an attacker can phish this component too, gaining account access effortlessly.
Yet, there are resilient authentication forms called phishing-resistant authentication or strong authentication.
Phishing-resistant authentication thwarts AiTM attacks by ensuring employees authenticate to websites with the correct domain name during login.
The technology for phishing-resistant authentication has existed for years but required additional hardware tokens for employees, posing adoption challenges.
Newer options, like passkeys, utilize similar technology as hardware tokens but use smartphones for phishing resistance.
Though passkeys offer advantages in preventing attacks, they are still new, with adoption in early stages.
**Device Compliance**
The approach to phishing resistance varies based on factors.
Given that phishing-resistant options are new, organizations may face challenges during implementation. Device compliance strategies might balance familiarity and security.
**Device-compliant authentication** restricts access, like Microsoft 365, to only known devices. If an attacker uses a phishing platform, authentication fails due to unregistered devices.
While most secure for organizations using company-owned devices, device compliance can also be adapted for personal devices under BYOD models, preserving privacy.
**Conclusion**
Threat actors will persist in accessing user accounts through ongoing phishing attacks. To adapt, consider this strategy:
1. **Centralize authentication by implementing Single Sign