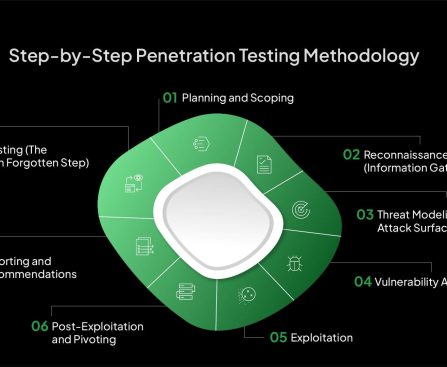
After wooing Cal AI for months, MyFitnessPal has successfully acquired its up-and-coming rival, Cal AI, the app built by teens soaring on the apps stores.
4 Creative Methods to Use the Micro-USB Port on Your Amazon Fire TV Stick
micro-USB port, which functions differently compared to a newer USB-C port, allows you to leverage additional features, or even power your Fire Stick by incorporating Ethernet support, increasing its limited storage, and more.
An Amazon Fire TV Stick provides users with access to countless apps via the Amazon App Store, enables interaction with Amazon’s Alexa voice assistant, and allows them to stream their favorite content without having to invest significantly more in an Apple TV 4K.
Although users should exercise caution regarding Amazon’s management of their privacy, and familiarize themselves with a few other considerations before purchasing an Amazon Fire TV Stick, once you acquire this device, you can enhance its capabilities through its micro-USB port by utilizing the following tips and tricks.
Ethernet support
Consumer Reports: Routers to Steer Clear Of Because of Low Performance and Unreliable Quality
best Wi-Fi routers or one of the higher-rated Wi-Fi mesh systems based on user feedback.
Netgear Nighthawk RAX41
The Nighthawk RAX41 by Netgear is a dual-band Wi-Fi 6 router that can accommodate up to 25 devices and is designed for gigabit internet connections. It includes four gigabit LAN ports and a single WAN port. Additionally, it boasts a USB 3.0 port for connecting storage devices such as a USB flash drive or an external hard drive. Notable features also incorporate support for Netgear’s Armor security solution, although the free trial lasts only 30 days. You can manage your Wi-Fi with Amazon Alexa or Google Assistant, and the router retails for $80 on Amazon.
These features certainly appear impressive. However, in its evaluation, CR discovered that the RAX41 exhibited below-average wireless speeds over long and mid-range distances, as well as inadequate speeds for near-range distances. Essentially, it doesn’t deliver
TikTok’s rival to Meta Quest set to debut in the US this year with an updated headset and revamped operating system.
Project Swan and Pico OS 6 are poised to transform the XR headset industry by tackling significant challenges encountered by current-generation devices. Pico, a subsidiary of ByteDance, is unveiling its headsets and software in North America for the first time, moving away from earlier restrictive launches. The forthcoming Pico OS 6 brings a total overhaul featuring a new spatial rendering engine, an updated UI, and robust open SDKs developed on Android Studio. This OS is designed to address existing XR OS issues by allowing standard Android applications to operate directly within immersive layers, improving interaction between 2D and 3D components.
Project Swan, a premium XR headset, is expected to deliver 40-45 pixels per degree (PPD) resolution, exceeding the current high-end options like Galaxy XR, which provide 35 PPD. This is accomplished using new micro-OLED screens with 4000 ppi resolution and bespoke silicon, ensuring enhanced visuals and performance. Pico’s specialized chipset doubles the CPU and GPU capabilities of existing chips such as Qualcomm’s Snapdragon XR2 Gen 2.
The headset is intended to supplant conventional monitors, delivering a fluid integration of virtual and physical realms. With compatibility for a variety of app ecosystems, including Spatial apps, OpenXR, WebXR, Android apps, and PC VR streaming, Pico’s innovative OS and headset are set to emerge as formidable contenders in the XR landscape, challenging established giants like Meta.
Apple Unveils the iPhone 17E
Apple has taken the wraps off the iPhone 17E, its latest entry-level smartphone. The iPhone 17E starts at $599 for 256GB of storage, and is available in black, white, and pink. The company revealed the new device as part of a series of announcements that kicked off this week. Similar to its predecessor, the iPhone […]
Important Alert: Numerous Wi-Fi Routers Vulnerable to AirSnitch Assault – Suggested Measures to Implement
**Comprehending the AirSnitch Vulnerability: Securing Your Wi-Fi Network**
In 2017, the WPA2 encryption protocol, commonly utilized by Wi-Fi routers, was breached, resulting in the emergence of WPA3. Nonetheless, a novel vulnerability identified as AirSnitch has arisen, presenting a considerable risk to Wi-Fi security. This article delves into the ramifications of AirSnitch, its likely effects on network security, and measures you can implement to shield yourself.
### What is AirSnitch?
AirSnitch is a recently uncovered attack technique that enables assailants to circumvent existing Wi-Fi encryption instead of dismantling it. Security experts state that this vulnerability facilitates a complete bidirectional man-in-the-middle (MitM) attack, permitting attackers to capture and examine all data flowing through the router. This encompasses sensitive information, even when sites are protected by HTTPS.
### The Dangers of AirSnitch
The main issue with AirSnitch is its capability to capture domain look-up traffic. Malefactors can leverage this to execute DNS cache poisoning, tainting the tables maintained by the target’s operating system. Furthermore, attackers can discern external IP addresses of accessed web pages, linking them with particular URLs. This presents a grave risk to both personal and sensitive information.
### Positive and Negative Aspects
The silver lining is that a perpetrator must initially know or decipher the SSID password to gain entry to the router. If you uphold a strong password for your home Wi-Fi network and restrict access to trustworthy individuals, your home network is considerably shielded from this vulnerability.
However, the scenario shifts dramatically when utilizing public Wi-Fi hotspots. These networks generally feature easily obtainable passwords, rendering them appealing targets for attackers. As a result, all traffic on public Wi-Fi is vulnerable, emphasizing the necessity of adopting further precautions.
### Safeguarding Yourself Against AirSnitch
To protect your network and personal information, consider these steps:
1. **Implement a Strong Password**: Ensure your home Wi-Fi router is secured with a solid password, including for guest access.
2. **Restrict Password Sharing**: Only share your Wi-Fi password with trusted visitors to reduce possible exposure.
3. **Employ a VPN**: When connecting to public Wi-Fi hotspots, always utilize a Virtual Private Network (VPN). This provides an additional security layer, encrypting your data and shielding it from potential interception.
### Conclusion
The identification of the AirSnitch vulnerability highlights the persistent challenges in preserving Wi-Fi security. While home networks can be strengthened with robust passwords and restricted access, public Wi-Fi continues to pose a considerable threat. By adhering to the suggested precautions, you can aid in protecting your data and maintaining your online privacy in an increasingly perilous digital landscape.
Currently, all evaluated routers are susceptible to AirSnitch, and it remains unclear whether a fix will be created to resolve this concern. Staying informed and vigilant is crucial in protecting your online identity.
Apple Unveils Latest iPad Air Equipped with M4 Chip, Together with C1X and N1 Variants
Apple has launched its major product announcement week today, revealing a new iPad Air equipped with the M4 chip. Here are the specifics.
## M4 iPad Air Update Highlights Enhanced Apple Silicon
Today, Apple has introduced a completely new iPad Air driven by the M4 chip.
The M4 is the most significant advancement in this new iPad Air, which retains numerous features from the previous M3 model released last year.
> “iPad Air provides users with more ways than ever to express creativity and enhance productivity, delivering strong performance and amazing versatility to help bring their ideas to life,” stated Bob Borchers, Apple’s vice president of Worldwide Product Marketing. “With its lightning-fast performance thanks to M4, remarkable AI capabilities, and transformative iPadOS 26 features, there’s never been a more opportune moment to select or upgrade to iPad Air.”
The primary fresh features Apple emphasizes with this new iPad Air are entirely linked to Apple silicon.
M4 represents a substantial enhancement for the main processor, boasting 50% more unified memory compared to the M3 model.
For cellular users, the iPad Air also transitions to Apple’s proprietary 5G modem: the C1X.
Apple first introduced C1X last autumn in the iPhone Air, and it subsequently appeared in the M5 iPad Pro as well.
One of the main advantages of C1X will manifest in battery efficiency if you are a heavy cellular user. Apple claims that C1X delivers “30 percent less modem energy consumption than the iPad Air with M3.”
The N1 wireless chip rounds out the trio of Apple silicon enhancements. It supports Wi-Fi 7, Bluetooth 6, and Thread. Apple also asserts that N1 “provides improved performance when connected to 5GHz Wi-Fi networks, and enhances the overall performance and reliability of features like Personal Hotspot and AirDrop.”
The new M4 iPad Air is offered in the same 11-inch and 13-inch sizes as earlier, and the same four colors: Space Gray, Blue, Purple, and Starlight.
Pricing begins at $599 for the 11-inch variant and $799 for the 13-inch, with additional charges for cellular compatibility.
Pre-orders will commence on Wednesday, March 4 at 6:15 a.m. PT. It will reach customers starting one week later, on Wednesday, March 11.
Are you planning to upgrade to an M4 iPad Air? Share your thoughts in the comments.
### Best iPad Accessories
Six Unique Bluetooth Devices for Sale
uncommon devices that utilize Bluetooth, these quirky Bluetooth gadgets are sure to pique your interest.
Liene PixCut S1
A compact photo printer that pairs with your device through Bluetooth and enables you to send designs from your mobile to be printed on the spot may not seem particularly bizarre. In reality, for those looking to preserve their cherished moments with premium laminated photo prints — which many standard printers fail to offer — the Liene PixCut S1 could be a fantastic purchase. It employs thermal dye-sublimation technology to print, laminate, and produce stunning, high-resolution 300 DPI prints. The advantage of this printer not requiring cartridges means you avoid spending excessively on ink or confronting troublesome smudges.
However
5 Expert-Recommended Tips to Streamline 3D Printing
frequent 3D printing pitfalls, such as distorted bases, chaotic supports, or other complications that lead to unsuccessful prints. If you’re just starting out in the hobby, the positive aspect is that numerous users have already discovered what is effective and what isn’t, making these insights simpler to implement.
There are various straightforward modifications that anyone can perform on their own 3D printer in a matter of minutes, yet each one contributes and significantly enhances the quality of each new print. From accurately adjusted slicer configurations to the selection of filament, these aspects may seem trivial initially, but they are crucial for achieving better outcomes. Thus, rather than relying solely on trial and error, concentrating on a few fundamental practices will aid in producing more dependable print results.
This indicates that a handful of enhancements in preparation, calibration, and material handling can frequently address the majority of challenges that newcomers to 3D printing encounter before they even manifest. Once the fundamentals are executed properly, each new endeavor shifts towards achieving improved outcomes rather than being preoccupied with potential failures.
Exercise caution with the initial layer
The Budget-Friendly MacBook: A Guide to the Mac Ecosystem
**The Future Affordable MacBook: A Transformative Shift for Apple**
Apple is poised to unveil a noteworthy announcement concerning an affordable MacBook, which the company anticipates will deliver “remarkable value.” This forthcoming product is likely to draw in two main user groups: individuals currently utilizing Windows or Chromebooks and iPhone users without a computer. The expected entry price of $599 might position this device as an appealing alternative to the current least expensive MacBook Air, which retails at $999.
### Target Audiences
1. **Users of Windows and Chromebooks**: Numerous laptop users are eager to own a MacBook but are discouraged by its steep cost. The budget-friendly MacBook could attract this segment, particularly those contemplating economical Windows laptops or Chromebooks within the $300 to $400 range.
2. **iPhone Owners Lacking a Computer**: There exists a portion of iPhone users who initially feel their device is adequate but may eventually desire a more powerful computing option. For those who have acquired an iPad with a keyboard, the affordable MacBook might represent an appealing next step.
### Facilitating the Shift
Transitioning from Windows to Mac has become considerably simpler in recent years. As most computing tasks are now executed through web apps and cloud storage, users can switch with limited support. This simplification of the transition is likely to motivate more individuals to explore the new MacBook.
### Acceptable Trade-Offs
To reach the low price point, the new MacBook might feature certain compromises, such as reduced RAM and possibly other specifications. However, initial feedback indicates that numerous potential users are open to accepting these concessions. Surveys suggest that while some users identify deal-breakers in the proposed features, a considerable segment remains enthusiastic about the new device.
### A Portal to the Mac Ecosystem
The launch of an affordable MacBook could serve as an entry point for new users into the Apple ecosystem. Once individuals enjoy the advantages of a Mac, they may be less inclined to revert to Windows. This could pave the way for future upgrades, establishing a valuable sales pipeline for Apple.
### Effects on the MacBook Air and Pro
The rollout of an affordable MacBook may also positively affect the current MacBook Air and MacBook Pro models. To stay competitive in the market, Apple may need to upgrade these versions, resulting in overall enhancements across the Mac lineup.
### Conclusion
The expected affordable MacBook signifies a strategic initiative by Apple to expand its user demographic and reinforce its market standing. With a competitive pricing strategy and the potential to entice new users, this device could profoundly affect the future of the Mac series. Comprehensive coverage of Apple’s announcements and hands-on evaluations will follow the official event.