Welcome to Tech Talk, your weekly resource for demystifying the technology that fuels your digital existence. This week, we’re exploring a subject that may seem daunting but becomes quite clear when you dissect it: malware.
What Is Malware?
Malware, short for “malicious software,” refers to any program or file intended to damage, exploit, or carry out unwanted actions on a device or network. It’s not limited to viruses — malware encompasses spyware, ransomware, adware, and trojans, among others.
In simple terms: if software is performing actions you didn’t authorize — such as stealing your contacts, tracking your location, or sending your data to others — it qualifies as malware.
For example: you download a flashlight application. Its sole purpose should be to activate your phone’s flashlight. However, if it requests access to your contacts or microphone, that’s a warning sign. Why would a flashlight application need to access your contacts?
How Does Malware Spread?
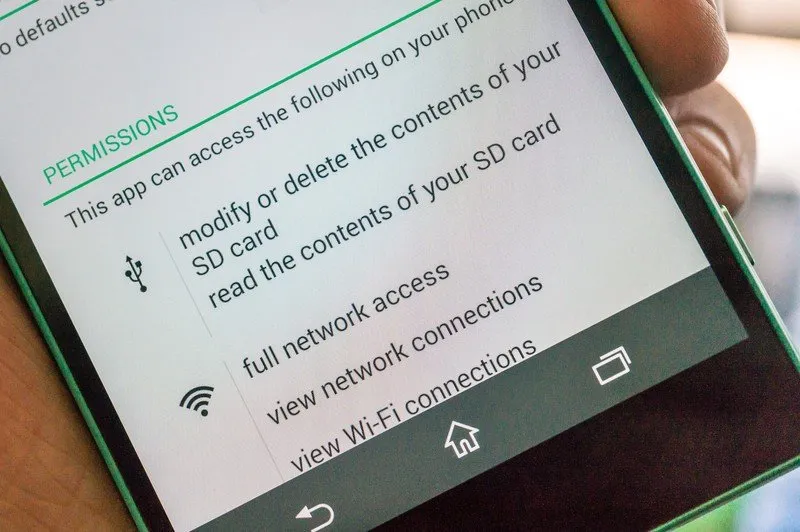
Malware can propagate in several ways, but here are the most prevalent:
- Via apps: Particularly those downloaded from unofficial app stores. Some apps only adhere to guidelines just enough for approval but introduce harmful behaviors through updates or concealed code.
- Social engineering: This occurs when you are deceived into clicking “yes” or “allow” without fully understanding what you’re consenting to. It’s akin to signing a contract without reviewing it.
- Exploiting vulnerabilities: Cybercriminals can leverage flaws in your device’s operating system to install malware unbeknownst to you. This might happen simply by accessing a compromised website or connecting to an unsecured Wi-Fi network.
Once malware infiltrates your device, it can do anything from bombarding you with annoying ads to stealing your identity or even converting your phone into a component of a botnet for cyberattacks.
How Can You Shield Yourself?

Here’s the encouraging news: safeguarding yourself from malware isn’t as challenging as it may seem. Adhere to these straightforward guidelines to remain protected:
1. Use Official App Stores
Whether you’re accessing Google Play, Apple’s App Store, or Samsung’s Galaxy Store, these platforms implement security precautions. They aren’t flawless, but they are significantly safer than downloading apps from unfamiliar websites.
2. Review Before You Click “Yes”
Always examine permissions and user agreements. If an app requests access to something unnecessary for its operation (like a calculator seeking microphone access), that’s a warning sign.
3. Keep Your Software Updated
Updates often incorporate security patches that rectify vulnerabilities. Postponing updates can expose your device to known threats.

