

# The Comeback of Necro Malware: Android Applications Compromised Once More
In a troubling turn of events, cybersecurity experts have once again discovered harmful Android applications on the Google Play Store, underscoring the ongoing menace of malware within the mobile sphere. After a similar occurrence five years ago, when a trusted Android application was covertly turned malicious, the cycle is repeating. This time around, two new applications, collectively downloaded more than 11 million times, have been identified as infected with the same malware family—Necro.
## The Discovery: An Unwelcome Repeat
The most recent findings were reported by researchers from the Moscow-based cybersecurity company Kaspersky. Their investigation revealed that the two compromised applications—**Wuta Camera** and **Max Browser**—boasted millions of downloads from the Google Play Store. Notably, Wuta Camera racked up over 10 million downloads, while Max Browser had about 1 million before it was taken down from the platform.
The infection originated from a malicious **software development kit (SDK)** utilized by the app developers, probably for the purpose of integrating ad functionalities. Nonetheless, this SDK also harbored hidden malware that facilitated communication with servers controlled by attackers, enabling the download of harmful payloads and the execution of malicious code on users’ devices.
## Mechanism of Necro Malware
Necro represents a highly evolved malware family that has developed over time. In this latest operation, the malware employs advanced techniques such as **steganography**—a strategy for concealing malicious code within seemingly harmless images. This method is rarely observed in mobile malware, rendering it exceptionally perilous and hard to detect.
### Discreet Communication and Payload Distribution
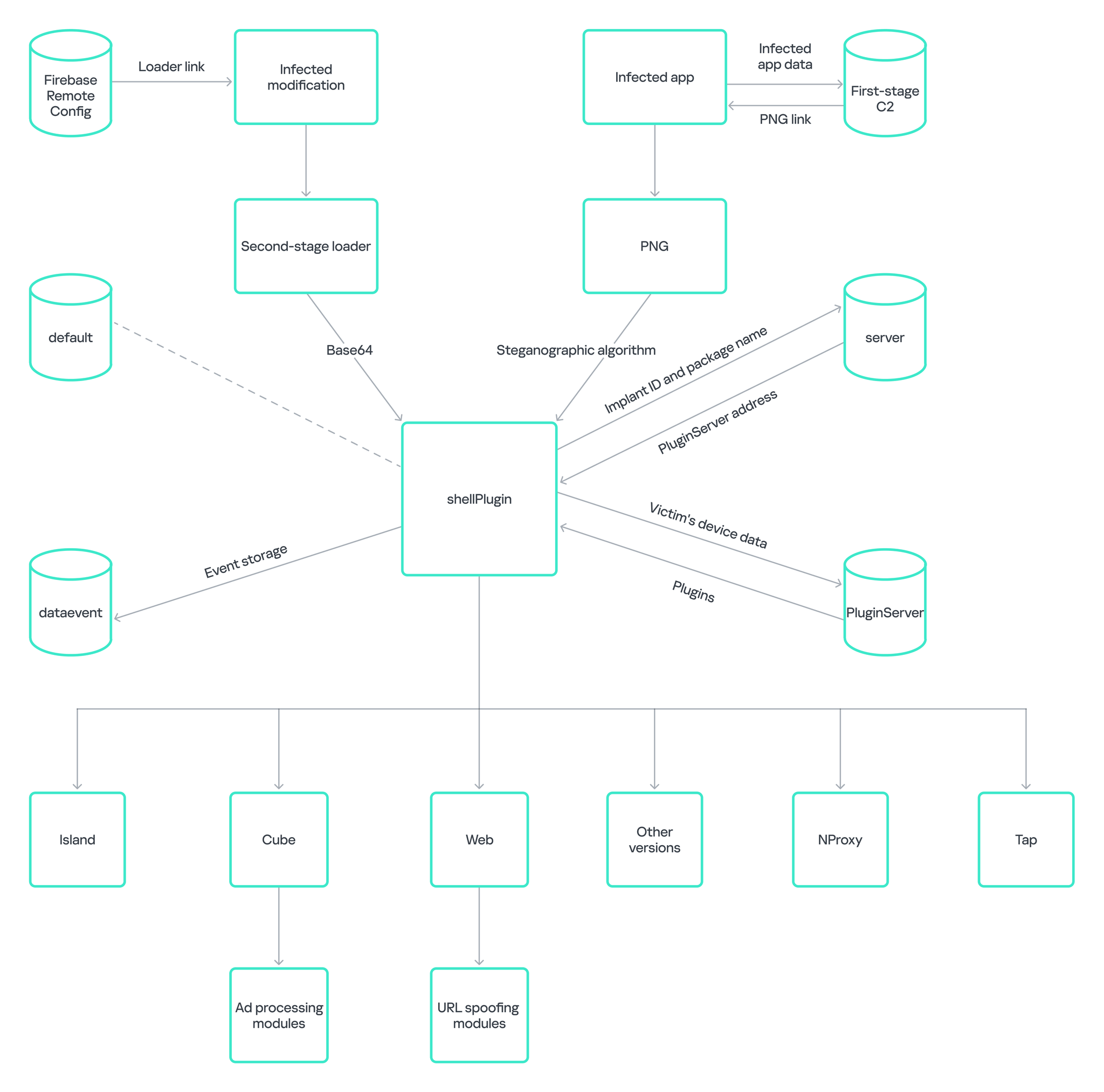
After an app infected with Necro is installed on a device, it starts communicating with a **command-and-control (C2) server** overseen by the attackers. The app transmits encrypted **JSON** data to the server, relaying details about the compromised device and the app using the malicious SDK. The server then sends back a link to a **PNG image** along with related metadata, including the image’s hash.
Once the infected app validates the hash, it proceeds to download the image. However, this image is not merely a standard photo. It conceals hidden code, which is extracted through a simple steganographic method. The malicious SDK utilizes standard Android tools to pull pixel values from the image’s **ARGB channels**. The least significant byte of the blue channel contains the encoded payload, which is subsequently decoded and executed.
### Modular Framework and Enhanced Privileges
Necro’s modular framework enables it to undertake an extensive array of malicious activities. The malware can fetch additional plugins, each crafted for specific functions. Some of these plugins permit the malware to operate with **elevated system rights**, granting it greater command over the infected device.
One of Necro’s gravest capabilities is its ability to circumvent Android’s security mechanisms. Typically, Android restricts privileged processes from accessing **WebView**, a feature that permits applications to render web content. However, Necro employs a **reflection attack** to generate a unique instance of the WebView factory, thereby evading this limitation.
After securing elevated rights, Necro can alter URLs, insert confirmation codes for paid subscriptions, and download as well as execute additional harmful code from attacker-managed servers. This capability furnishes attackers with the means to perpetually update the malware and tailor its operations based on the specific device it has compromised.
## The Extent of the Infection
Kaspersky’s researchers pinpointed Necro in two primary applications available on the Google Play Store:
1. **Wuta Camera**: Versions 6.3.2.148 through 6.3.6.148 of this widely-used camera app were found to contain the malicious SDK. The app has since been updated to eliminate the harmful component.
2. **Max Browser**: This application, which secured around 1 million downloads, was also infected with Necro. It has since been removed from the Google Play Store.
Beyond these two applications, the researchers detected Necro in several Android applications hosted on **alternative app marketplaces**. These applications often masqueraded as modified editions of legitimate apps, including well-known titles such as **Spotify**, **Minecraft**, **WhatsApp**, **Stumble Guys**, **Car Parking Multiplayer**, and **Melon Sandbox**.
### Diagram of Necro’s Infection Mechanism
Kaspersky presented a comprehensive diagram depicting the infection mechanism of Necro, illustrating how the malware interacts with the C2 server, retrieves payloads, and executes harmful code. The modular characteristics of Necro permit it to adapt to various devices and circumstances, rendering it a versatile and formidable threat.
## The Necessity for Caution
The revival of Necro emphasizes the ongoing difficulties in safeguarding the Android ecosystem. While Google has made notable progress in enhancing the security of the Play Store, malicious applications continue to evade detection, often employing sophisticated techniques like steganography.